What is a SCAP Scan
SCAP stands for Security Content Automation Protocol. SCAP scans compare the system you are scanning to a baseline (benchmark) which are open security standards of security to find compliance or non-compliance of system. It uses specific standards to help organizations automate the way they monitor system vulnerabilities and make sure they’re in compliance with security policies.
More information on the SCAP tools and using the benchmarks in the SCAP scan process can be found at https://public.cyber.mil/stigs/scap/.
The SCAP Scan Process
The SCAP benchmarks are available as ZIP downloads on this site as well. The DISA SCAP scan is available to be downloaded from the DoD Public Cyber Exchange NIPR site. See the URL above for more information. You use the benchmark files to load into the SCAP scanner and that allows the scan to match against good known security standards. The results of a SCAP scan can be exported as an XCCDF format XML file and then imported into a Checklist using a tool such as STIG viewer or OpenRMF® Professional to create an actual checklist of findings.
Tenable’s tool Nessus also has a SCAP scan capability for SCAP scans that covers a subset of the scans that the NIWC SCAP Scanner can do. You also can export those files as XCCDF Format and import into OpenRMF® Professional to create a checklist of findings as well. Please make sure to use a DISA benchmark and choose the correct profile for matching to XCCDF format for your XML results file.
You also can use the OpenSCAP (https://www.open-scap.org/) application to also scan based on SCAP 1.2 or 1.3 formats for specific Red Hat based Linux operating systems. Please make sure to use a DISA benchmark and choose the correct profile for matching to XCCDF format for your XML results file.
OpenRMF® Professional can also read XCCDF SCAP Scan results from Rapid 7 Nexpose. You can export XCCDF SCAP Scan files from your SCAP scans in Nexpose that save the SCAP data with the report for rule results. These file types can be used in the System Package area of uploading checklists. Please make sure to use a DISA benchmark and choose the correct profile for matching to XCCDF format for your XML results file.
You also can upload SCAP Scan results from HBSS scan results in .xml files. Additionally, using Tanium SCAP results in .csv files is also allowed. These file types can be used in the System Package area of uploading checklists. Please make sure to use a DISA benchmark and choose the correct profile for matching to XCCDF format for your XML results file.
Note: the maximum allowed file size when uploading checklists and scans is 100 MB, and up to 20 files at a time. This limit is placed for timeout purposes and processing of large combined files creating multiple checklists with a single upload.
Note that your SCAP scans need to use a DISA benchmark to match to the DISA checklists within OpenRMF® Professional. An example syntax using openSCAP is below:
sudo oscap xccdf eval \
--profile xccdf_mil.disa.stig_profile_MAC-3_Sensitive \
--results myrel8machine-hostname-xccdf.xml \
./U_RHEL_8_V1R8_STIG_SCAP_1-2_Benchmark.xml
Turning a SCAP Scan into a Checklist
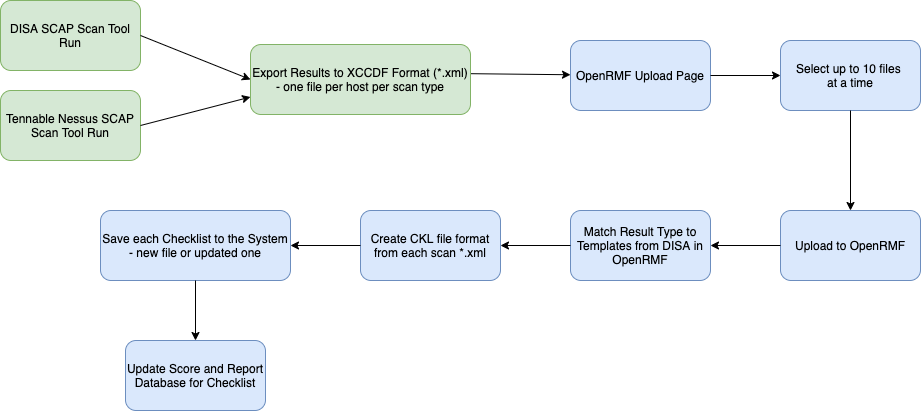
A scan by itself is great. However, it needs to be turned into a checklist to show proof and get actionable results. The best way involves creating your checklist from the exported SCAP Scan in XCCDF format based on a proper benchmark and uploading into OpenRMF® Professional. If you use the Upload feature and upload a SCAP result file, OpenRMF® Professional will match the SCAP scan to the proper checklist template and create your Checklist for you.
For a brand new SCAP scan (it is not already a checklist in the system package), all items matching the Open, Not a Finding and Not Applicable from automated SCAP scan results are updated in the proper checklist file. Then the checklist is added to your System Package you upload into, and the results are available within seconds. You also will see the generated “score” of the total Category 1, 2, and 3 items grouped by their status. All other items are marked as Not Reviewed. The Finding Details is updated for all found vulnerabilities that are Open or Not a Finding (not counting locked vulnerabilities) to show the scanner, date and time, and status.
For a SCAP scan that is updating a checklist already in the system package, OpenRMF® Professional will update vulnerabilities matching the Open, Not A Finding or Not Applicable status that are automatically checked via the SCAP, minus any locked vulnerabilities on that checklist. All other vulnerability items are left alone. Only the Status field and Finding Details field are updated according to the SCAP scan results when updating a checklist already in your system package. If you wish to use SCAP to update your checklists, put all your comments in the Comments field as the Finding Details field is updated with SCAP findings automatically.
As stated previously, if you are updating a checklist that has locked vulnerabilities those vulnerability records are not edited and are skipped. For any checklist that is locked at the checklist level, all SCAP scan results are skipped and the checklist is left as is.
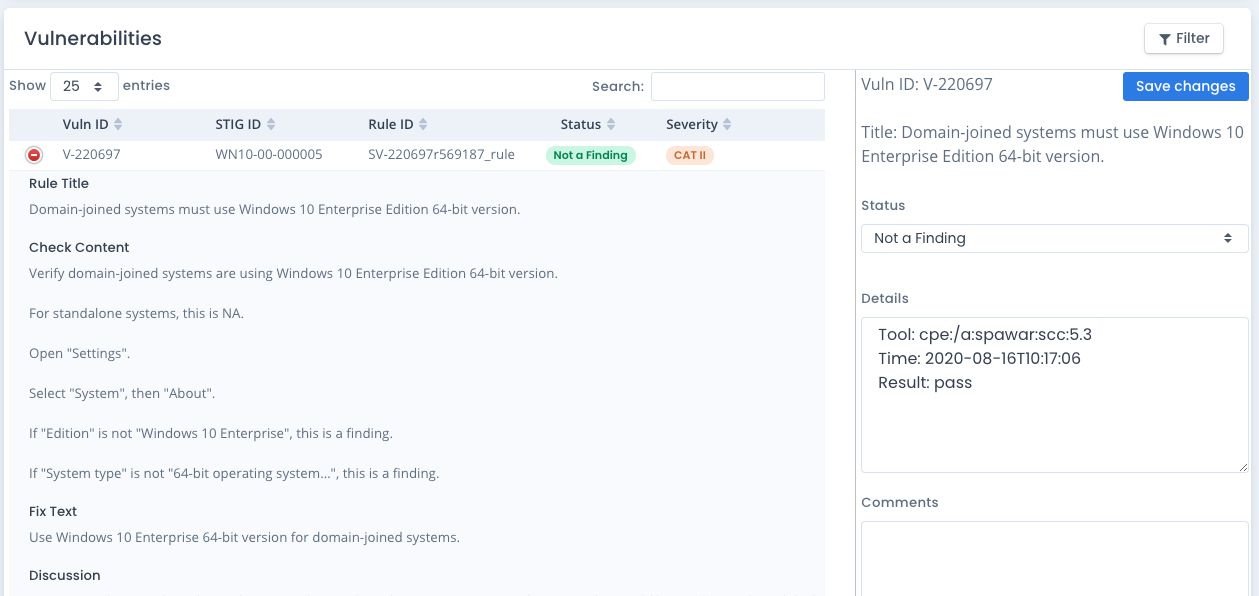
If you upload an updated SCAP scan, based on the type of benchmark and the hostname your results will be updated. Otherwise, this process creates a brand new checklist and adds it to the System you chose. For all automated checks, the details section will show the tool, the time, and the result for each vulnerability entry as shown below.
The checklists you make per system per operating system or software application (i.e. one for MS Office, one for Windows 10, one for Windows defender, all on the same machine) are used as evidence of your security posture. You do this when going for compliance, security checks, or a DoD or Federal Government ATO to get your system or network connected to the infrastructure and in production.
Example of using a SCAP Scan
Understand that a SCAP scan “normally” will only have a subset of standards to perform on a system. To really understand the security compliance of your system, you need to take the results and import them into a checklist file of the same product. An example would be to perform a SCAP scan of a system using a Windows 10 Benchmark and then import the results into a Windows 10 checklist.
OpenRMF® Professional performs this function if you upload your SCAP scan results. The checklist will have the full set of security compliance items and when you import the SCAP results it will update the blank checklist with its findings. You will then go through the rest for applicability to your system. That includes any checks that cannot be done in an automated fashion that must be checked manually.