View a Checklist Record
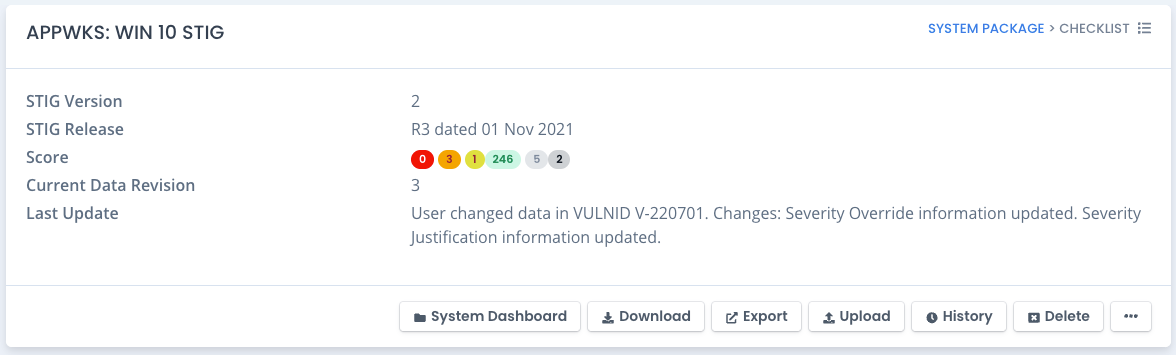
To view checklist information you click the linked title on the System page or choose View from the ... menu in the checklist listing table. The checklist page shows up and information is displayed in a few areas. The top area shows the checklist STIG type (SQL Server, Windows 10, Red Hat Linux, etc.) as well as the version and release number of that checklist from DISA, CIS or Custom creation.
It will also show the “Current Data Revision” which shows how many updates have been on your checklist. The revision starts at 1 for newly uploaded or created checklists and goes up from there.
The Checklist Score at the top is also a linked filter for the vulnerabilities. It is similar to clicking the Filter button above the vulnerabilities and specifying options. For example, click the 2nd number which is the Open Category II / medium vulnerabilities and the vulnerability listing is filtered based on just those options.
Checklist Main Data
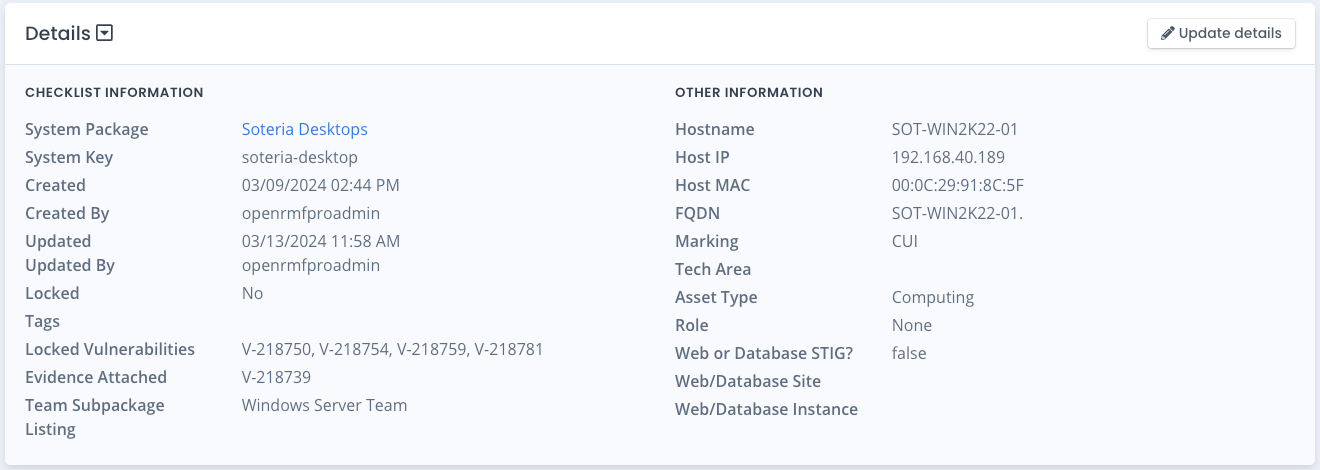
The second area of the checklist area shows the system information this checklist is associated with and the date and time it was created. It also shows the user who created this checklist for tracking and auditing purposes. The updated information, if any, is also here. The right side shows the hostname, fully qualified domain name, the markings (classification) and other data on the overall checklist.
This area also shows a list of any locked vulnerabilities, vulnerabilities with evidence attached, as well as any Team Subpackages containing this checklist.
Checklist Vulnerabilities
The bottom section of the checklist page shows a table of all vulnerabilities. You can use the next and previous page buttons to cycle through the data. The search box allows quick filtering client side and you can also sort the columns by clicking on the column headers. If you have proper rights the checklist vulnerability rows have a ... menu button to allow editing the vulnerability information. That is detailed in the Checklist Vulnerabilities Help Area.
Editing Checklists
When you edit checklists you can update the main details such as the hostname, fully qualified domain name, tech area, asset type, and role. You also can update the Host IP and MAC Address as well as set the web or database information, if any. This information is saved with the checklist data and viewable on the checklist page.
You also can add one or more tags for viewing and filtering on the system checklist listing page. And you can specify if this checklist is for a non-host related subject such as a process, procedure or documentation related checklist.

Downloading a Checklist
You can download a checklist one at a time from this page. Choose the download button at the top choose to download a .ckl or .cklb format file. The naming of the file should include the system key, the hostname or device name, and the type of checklist so it is quickly understood as to the data it contains.
You can also export a checklist to MS Excel .xlsx file one at a time from this page by choosing the XLSX format from the download options. The naming of the file should include the system key, the hostname or device name, and the type of checklist so it is quickly understood as to the data it contains. The rows in the spreadsheet are color coded according to the status and severity of the vulnerability item, similar to the score colors for the same status and severity.
Note that the checklist XLSX will use the current vulnerability filter if you have set certain status and severity to show and hide.