OpenRMF® Professional Compliance Overlays
The Overlays area allows Administrators to create and edit compliance overlays. These overlays when added to a system package update the SSP Control to Vulnerability Matrix as well as the Compliance Engine when generating the compliance listings. Overlays are combined with regular framework controls based on your framework version and any levels specified for generating compliance.
Alternatively, if you are tailoring your controls they are combined with the tailored list of controls for the same purpose.
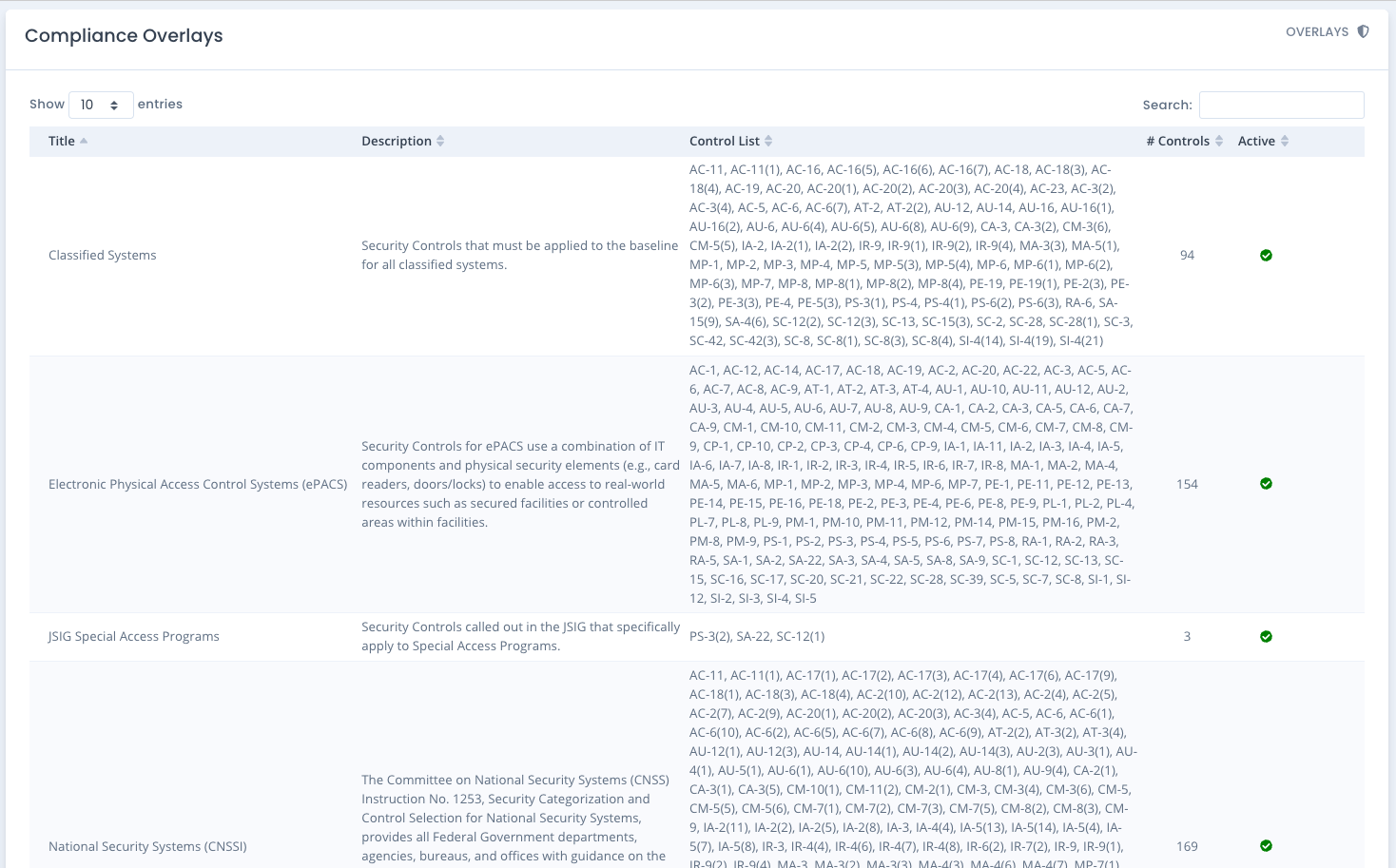
Listing Overlays
When you go to the Administration level Overlay screen it displays any overlays and shows the title, description, list of controls and if it is active. On the far right of each listing is the ... menu to allow editing or downloading of the full overlay to a JSON file.
Creating Compliance Overlays
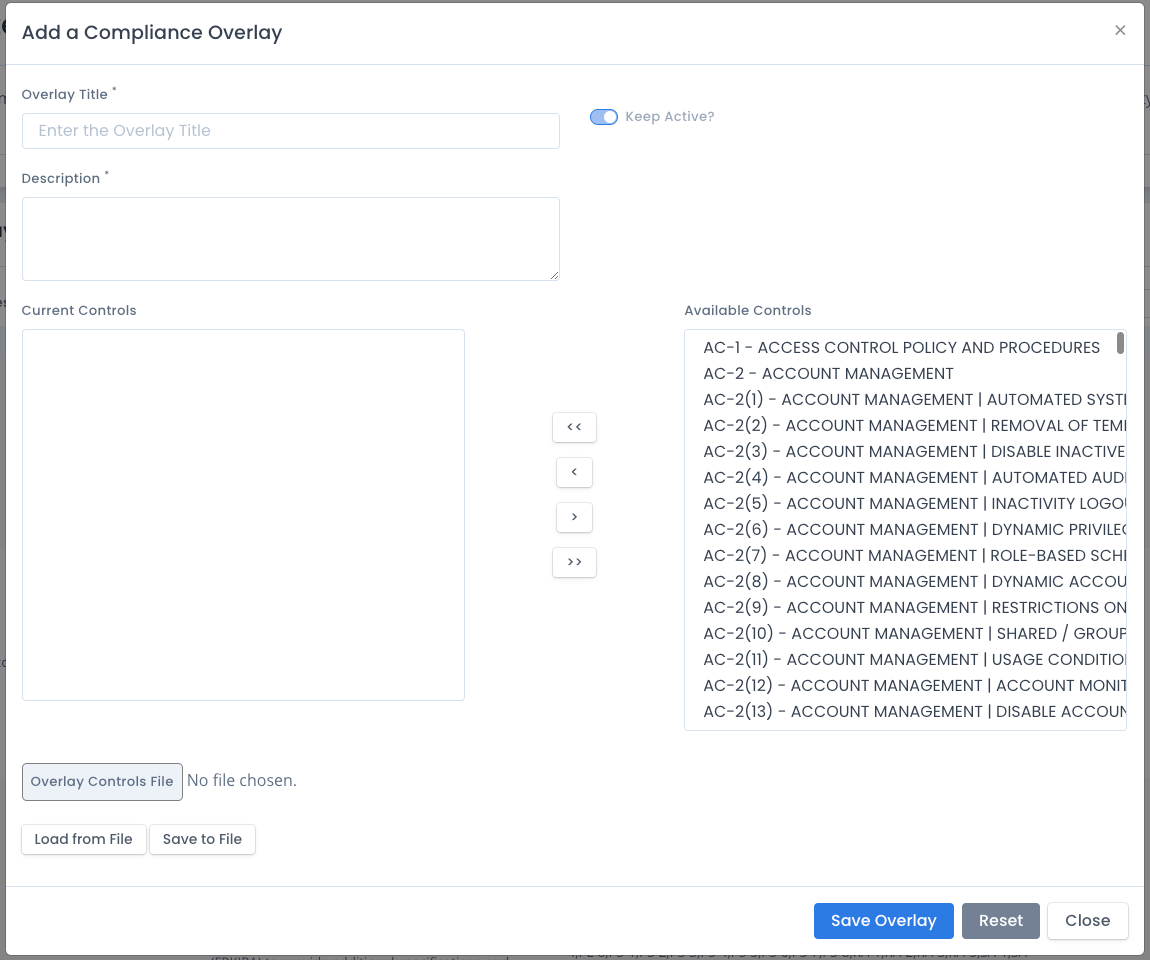
To create a new overlay you click the Create button. You enter a title, a description, then select a Framework Type. When the controls are loaded, click the arrow buttons to move the Available Controls to the Current Controls in the overlay.
There are no controls filtered out in the Available Controls. It is a listing of all the controls based on the framework selected, regardless of any levels available.
NOTE: Once a compliance overlay is created it can be marked active or inactive, but not removed just in case others are wanting to reference it. Only active compliance overlays are used to affect compliance generation and SSP generation in a system package.
Creating an Overlay by Uploading a JSON file
You also can upload a saved .json file downloaded using the “Download” menu option listed mentioned above. Click the Overlay File button on the Add a Compliance Overlay screen. Select the file from your file listing window and select Open to upload the file. A prompt will warn you all edited data will be replaced. Click OK to load that overlay and listing and edit and/or save it to use it in your system package.
The JSON structure is shown below:
{
"frameworkWithVersion":"RMF Revision 5",
"overlayTitle":"Program Overlay",
"overlayDescription":"The required Program Overlay",
"overlayControls":[
"SR-10","SR-11","SR-11(1)","SR-11(2)","SR-11(3)","SR-12","SR-8","SR-9","SR-9(1)"
]
}
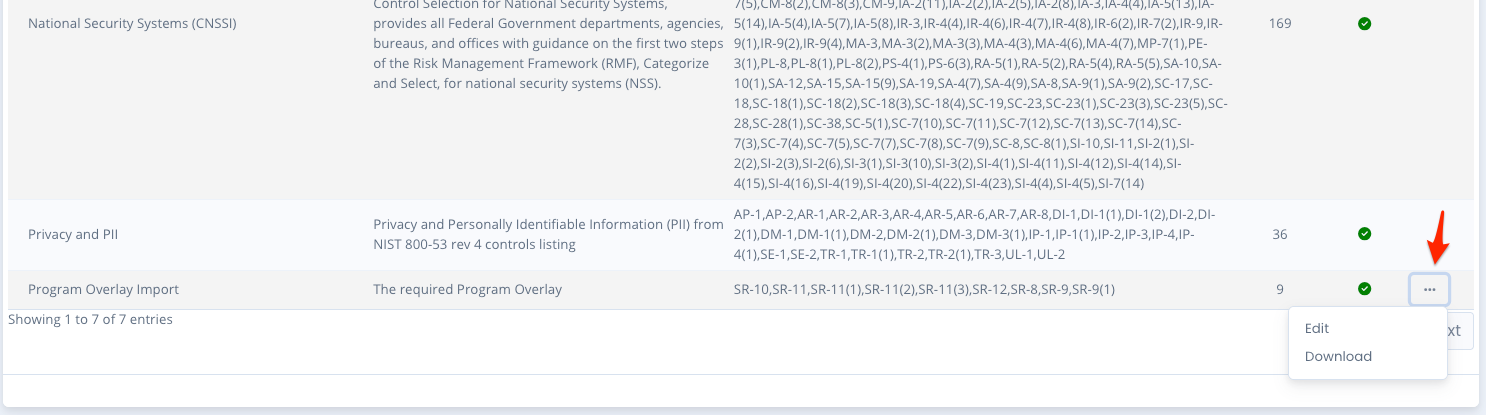
Editing an Overlay
To edit an overlay click the ... menu beside it and select the Edit option. Edit the title, listing, description or mark it Active or Inactive. Then click the Save button. This only saves it at this level. If any person has added an application-wide overlay to their system package they will have to adjust it at the package level.
You can only edit an overlay you have created. You cannot edit any default overlays.
Included Default Overlays
There are six (6) overlays by default created at the Administrator level based on NIST 800-53 controls. These can be used within any system package and are included by default in the available listing. They cannot be removed. They can be added to a system package and from there can be edited or altered as required by that system package.
- CNSSI - The Committee on National Security Systems (CNSS) Instruction No. 1253, Security Categorization and Control Selection for National Security Systems, provides all Federal Government departments, agencies, bureaus, and offices with guidance on the first two steps of the Risk Management Framework (RMF), Categorize and Select, for national security systems (NSS).
- DoD Privacy and PII - Privacy and Personally Identifiable Information (PII) from NIST 800-53 rev 4 controls listing
- Classified Systems - Security Controls that must be applied to the baseline for all classified systems.
- Electronic Physical Access Control Systems (ePACS) - Security Controls for ePACS use a combination of IT components and physical security elements (e.g., card readers, doors/locks) to enable access to real-world resources such as secured facilities or controlled areas within facilities.
- JSIG Special Access Programs - Security Controls called out in the JSIG that specifically apply to Special Access Programs.
- Federal PKI - Security Controls called out for the Public Key Infrastructure