Ports, Protocols, and Services Management
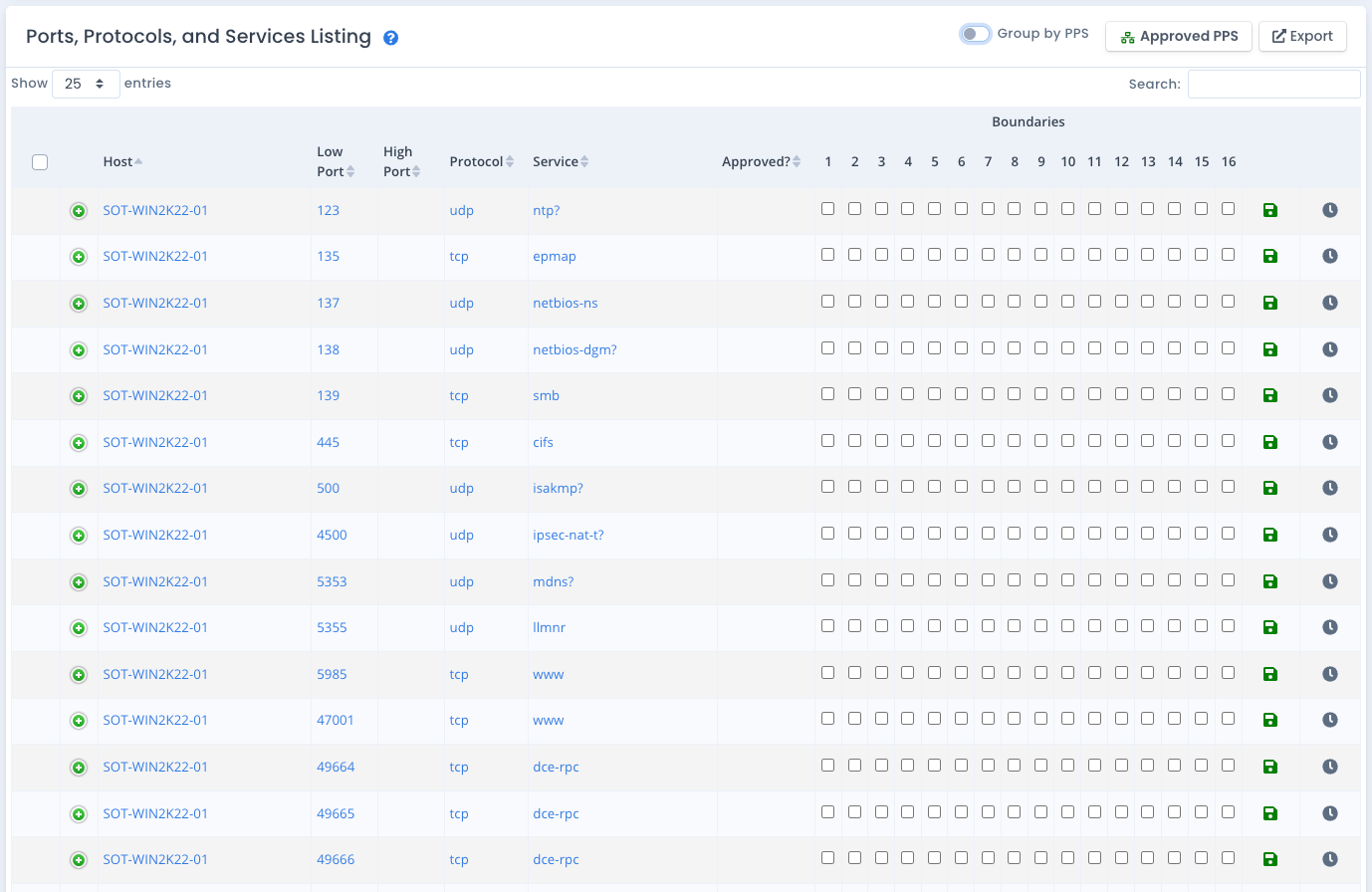
The Patch Scan uploads record all ports, protocols, and services for each device scanned. This information is pulled from the scans and saved by server to show which ports, protocols, and services are currently running on that device. This allows users who have Patch Administrator or System Owner rights to track the inbound and outbound access these services have over the network.
The list of boundaries and the inbound and outbound descriptions are available with the help icon next to the table title.
To update the boundary information, you click the checkbox if it crosses that boundary. Then click the green save icon to the right in that row. The information is saved, the older record is saved for tracking and versioning, and any new listing or report will reflect that information immediately.
For those without rights to edit the data, they see an “X” in the column for the boundary crossed where it is applicable. The clock icon to the far right of each row shows edit history over time of that particular PPSM entry based on scans and manual updates of the boundary information.
Example DoD Boundary Information is as follows:
- Boundary 1/2 - Network traffic that flows directly to and from an external, non-DoD network to a DoD Network (major network structures managed by DoD to include NIPRNet, SIPRNet).
- Boundary 3/4 - Network traffic that flows to and from an external network to a DoD-controlled DMZ. NOTE: A DoD DMZ is a screened subnet between a DoD network and an external non-DoD network. The DoD DMZ also acts as a special purpose gateway setup to proxy certain types of traffic to/from an external non-DoD network. Not all traffic goes to or passes through a DoD DMZ.
- Boundary 5/6 - Network traffic that flows to and from a DoD DMZ into a DoD Network.
- Boundary 7/8 - Network traffic that flows to and from a DoD Network directly into an enclave. An enclave represents a collection of computing environments connected by one or more internal networks under the control of a single authority and security policy, including personnel and physical security, with primary connection to a DoD network. The most common example is a single military service installation LAN connected to the NIPRNet. Other examples include a base, post, or command. (Note: this DOD Boundary is also referred to as the Navy B1)
- Boundary 9/10 - Network traffic that flows to and from a DoD Network to an enclave DMZ. The enclave DMZ is a screened subnet that hosts public accessible services/activities for both external and internal networks, thus enforcing two separate security policies.
- Boundary 11/12 - Network traffic that flows to and from an enclave DMZ to the internal nclave. You may also use these boundaries to indicate traffic to/from a legacy network or COI to NMCI (traffic that does not cross the DISN/DODIN), or between systems within the enclave that does not cross the DISN/DODIN.
- Boundary 13/14 - Network traffic that flows to and from an enclave directly to a non-DoD network, typically through a dedicated communications channel or leased line.
- Boundary 15 - Boundary 15 (Enclave-to-Enclave) represents a NIST FIPS 140 validated or NSA approved VPN tunnel (i.e. a site to site tunnel between enclaves) under the authority of multiple DAAs. The connection will be considered a Boundary 15 if the hosting Enclave exercises active control and enforces their security policy on the traffic contained within the VPN (i.e. filtering and blocking based on hosting Enclave policy)
- Boundary 16 - Boundary 16 (Enclave-to-Enclave) represents a NIST FIPS 140 validated or NSA approved VPN tunnel (i.e., a geographically distributed extension of the Enclave) under the authority of the same DAA. The connection will be considered a Boundary 16 connection if the hosting Enclave only breaks the tunnel for inspection but exercises no control or policy enforcement on the traffic within the VPN (i.e. passive monitoring)
You can use this listing above or create your own mapping of what 01 through 16 means within your network topology.
Exporting the PPSM Listing to MS Excel
Click the Export button just to the right of the table listing to download all the data into a MS Excel (XLSX) spreadsheet containing all the information seen in the table. This can be used for data calls, reporting, and other requirements outside of using OpenRMF® Professional.