Uploading Technology Vulnerabilities
You can upload technology vulnerability data to OpenRMF® Professional as well. You must have the System Owner or Vulnerability Administrator permission to use this feature. To go to it, from the system package dashboard click on the Other Technologies menu and choose the Upload Vulnerability Scan Data option.
The format of the data required is at the bottom of this page for you to do any ETL or transforming of data to match. As we get more native imports available we will update the software and documentation to match.
Uploading Data
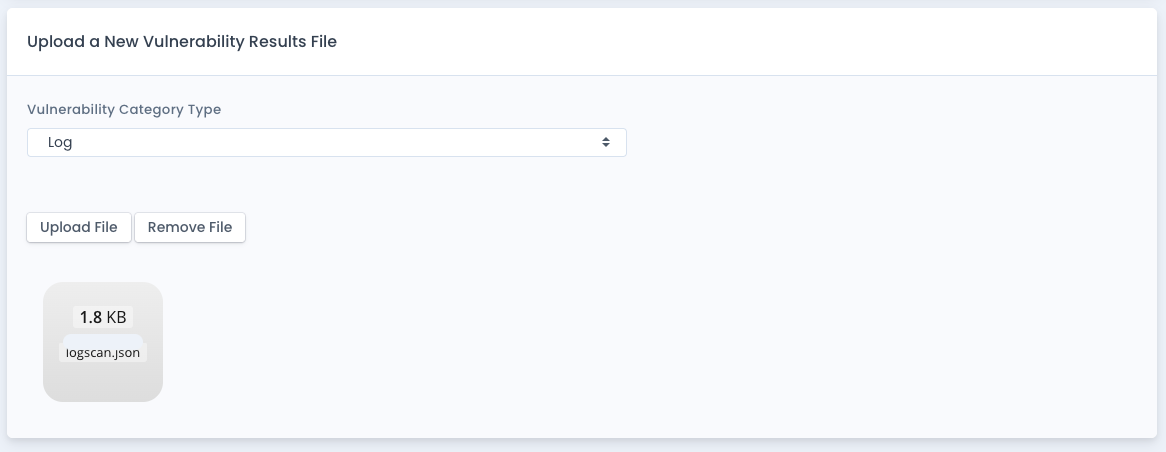
On the Upload Vulnerability Results page you specify the category type of Software, Container, Log or Other. Then drag and drop a file or click in the file area to select a valid JSON file with the results. Click the Upload File button to upload the file and process it for your system package. The data is parsed, saved, and the score for the source projects in the file are generated. Then all automation below kicks in.
OpenRMF® Professional can natively read in .xml scan result files from Burp for software scans.
We also take in Trivy container image scans in .json output files when running a command similar to trivy image {image-name}:{tag} -f json > {filename}.json to get results in JSON format.
We take in Grype container image scans in .json format files when running a command similar to grype {image-name}:{tag} -o json > {filename}.json as well.
We take in Amazon ECR container image scans in .json files when running a command similar to AWS_PROFILE={profile name} aws ecr describe-image-scan-findings --no-paginate --repository-name {ECR repo name} --image-id imageTag={imageTag} > {filename}.json.
We take in Artifactory JFrog CLI container image scans in .json formatted files when running a command similar to jf docker scan {image-name}:{tag} --format json > {filename}.json.
And we take in RapidFort CLI container image scans in .json formatted files when running a command similar to rfscan soteriasoft.jfrog.io/openrmfpro/openrmfpro-api-artifact:2.13.07 --reports-folder v2.13-openrmfpro-api-artifact. The folder will contain the vulnerabilities JSON file along with other files.
Otherwise, you can import data directly or use the general format listed below for vulnerability data.
Automation from Uploading Data
Once the technology vulnerability data is uploaded, there are several automated actions that are started. This is the same as when you import data.
The score generated is used to update the total technology vulnerability score for all projects for the specific category of data you imported. And then the total vulnerability score across all categories and source projects is updated as well. This data will be available in seconds on the scores page for this area.
If you have a live POAM created, any updates on vulnerability data is tracked in the POAM as well. Any items that are marked as Open or Won’t Fix are set as Open in the POAM. And any items already on the POAM that are now not Open or Won’t Fix are marked as Completed automatically with the date of the import as the completed date.
Format of General Format JSON Data
The format of the data required is just below in the case of a general JSON format that OpenRMF® Professional can universally ingest. It is a JSON format of data in an array, where each object is in essence the class structure to hold the technology vulnerability data. The list of values / enumeration information is at the bottom of the page.
[
{
"issueId": string,
"severityType": severityType,
"statusType": statusType,
"component": string,
"project": string,
"projectVersion": string,
"source": string,
"line": int,
"message": string,
"description": string,
"issueCreationDate": string,
"issueUpdateDate": string,
"organization": string,
"resolution": resolutionType,
"issueUrl": string,
"categoryType": categoryType,
"cvssScore": decimal
},
{
...
}
]
An example data payload is below for a software scan results file
[
{
"issueId": "CVE-2024-12345",
"severityType": 40,
"statusType": 50,
"component": "mysoftware-container-zsasdfasjfd-xxsad",
"project": "my-repo-name",
"projectVersion": "latest",
"source": "Snyk",
"line": 0,
"message": "Known vulnerability xyz is present in this container image",
"description": "A use-after-free vulnerability was discovered in xasprintf function in xyz component",
"issueCreationDate": "02/01/2025 09:49:40",
"issueUpdateDate": "02/21/2025 13:11:59",
"organization": "myorg",
"resolution": "",
"issueUrl": "",
"categoryType": 20,
"cvssScore": 3.5
},
{
"issueId": "CVE-2025-01269",
"severityType": 20,
"statusType": 50,
"component": "mysoftware-container32-zsasdfasjfd-xxsad",
"project": "my-repo-name",
"projectVersion": "latest",
"source": "Snyk",
"line": 0,
"message": "Known vulnerability aa33 is present in this container image",
"description": "A use-after-free vulnerability was discovered in aa33_remote() function in aa33 component",
"issueCreationDate": "02/01/2025 09:49:40",
"issueUpdateDate": "02/21/2025 13:11:59",
"organization": "myorg",
"resolution": "",
"issueUrl": "",
"categoryType": 20,
"cvssScore": 7.0
}
]
For the categoryType field you have these options:
- Software = 10
- Container = 20
- Log = 30
- Other = 40
For the severityType field you have these options:
- Info = 10,
- Low = 20,
- Medium = 30,
- High = 40,
- Critical = 50
For the statusType field you have these options:
- Closed = 10,
- FalsePositive = 20,
- Fixed = 30,
- WontFix = 40,
- Open = 50
Specifically for the SonarQube ResolutionType, you have these options:
- Fixed
- False-Positive
- FalsePositive
- WontFix