Viewing POAM Listings
Your Team Subpackage POAM shows any open checklist or patch POAM item linked to a checklist or host/device in your team subpackage. It is normally a subset of the larger system package POAM.
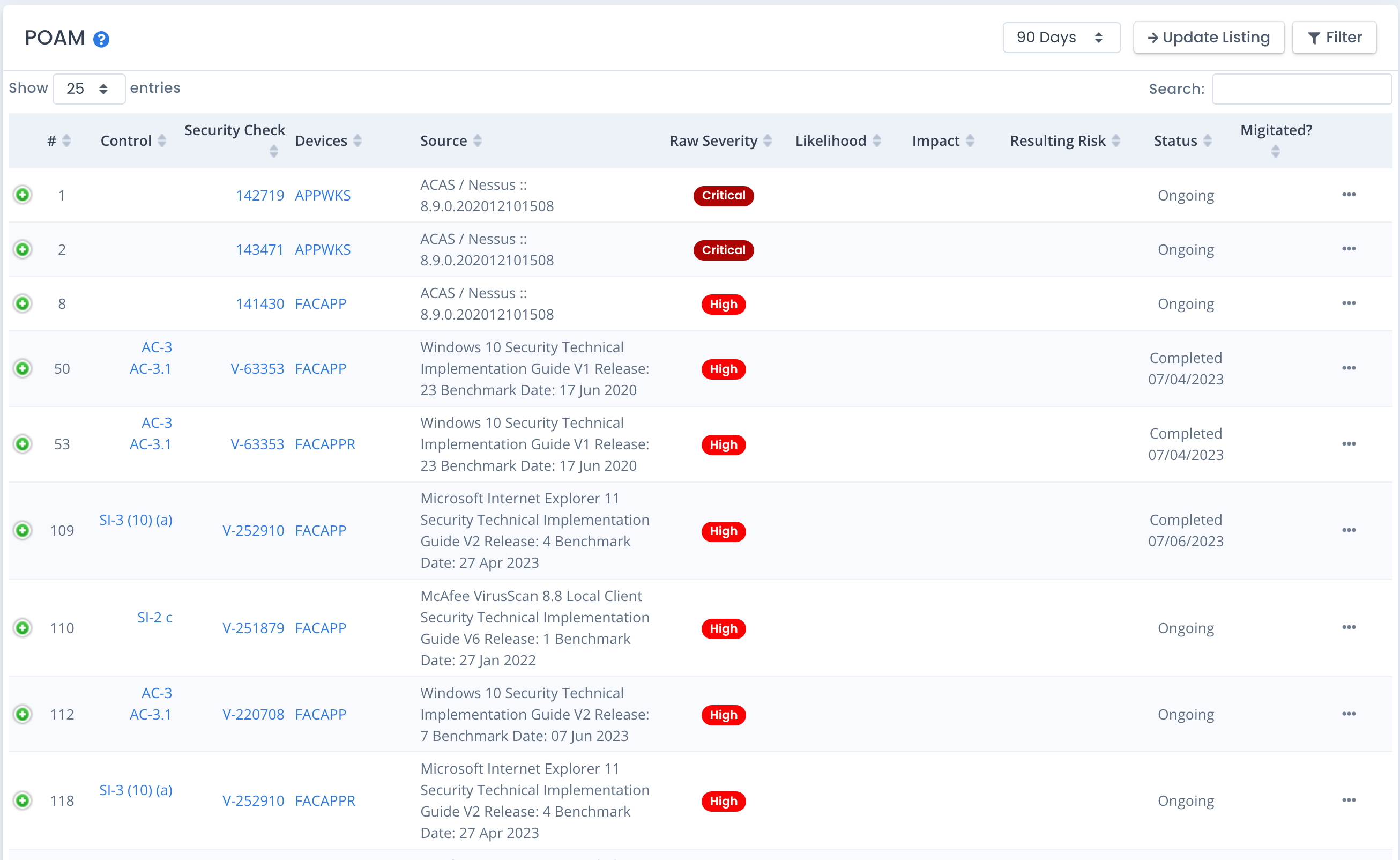
You can filter the POAM by selecting the 30 / 60 / 90 day filter. If you want to view all data you can choose the All option. Data is sorted by the Overall Residual Risk, then the Raw Severity, and grouped by patch vulnerabilities and then checklist vulnerabilities within each of those risk and severity levels.
Note the POAM contains one line per vulnerability per device / checklist / scan project for traceability and automation purposes. This may make your POAM look very large for system packages that have many devices or checklists with open vulnerabilities. This is for detailed display purposes and traceability for the automation of opening and closing POAM items.
If your POAM entry contains any evidence files attached, a paperclip icon will show in the POAM row listing to notify you there is evidence attached to that POAM record.
If your POAM has a scheduled completion date within 30 days and is still Ongoing, it also shows a calendar icon for a quick visual noting this. The calendar is colored red if the date is past due.
The ordering is as follows for the web listing and the MS Excel export:
- Very High Overall Residual Risk
- Critical Patch Vulnerabilities
- Critical Manual POAM items
- High Overall Residual Risk
- High Patch Vulnerabilities
- High Checklist Vulnerabilities
- High Manual POAM items
- Moderate Overall Residual Risk
- Medium Patch Vulnerabilities
- Medium Checklist Vulnerabilities
- Moderate Manual POAM items
- Low Overall Residual Risk
- Low Patch Vulnerabilities
- Low Checklist Vulnerabilities
- Low Manual POAM items
- Very Low Overall Residual Risk
- Very Low Manual POAM items
Filtering the POAM Listing
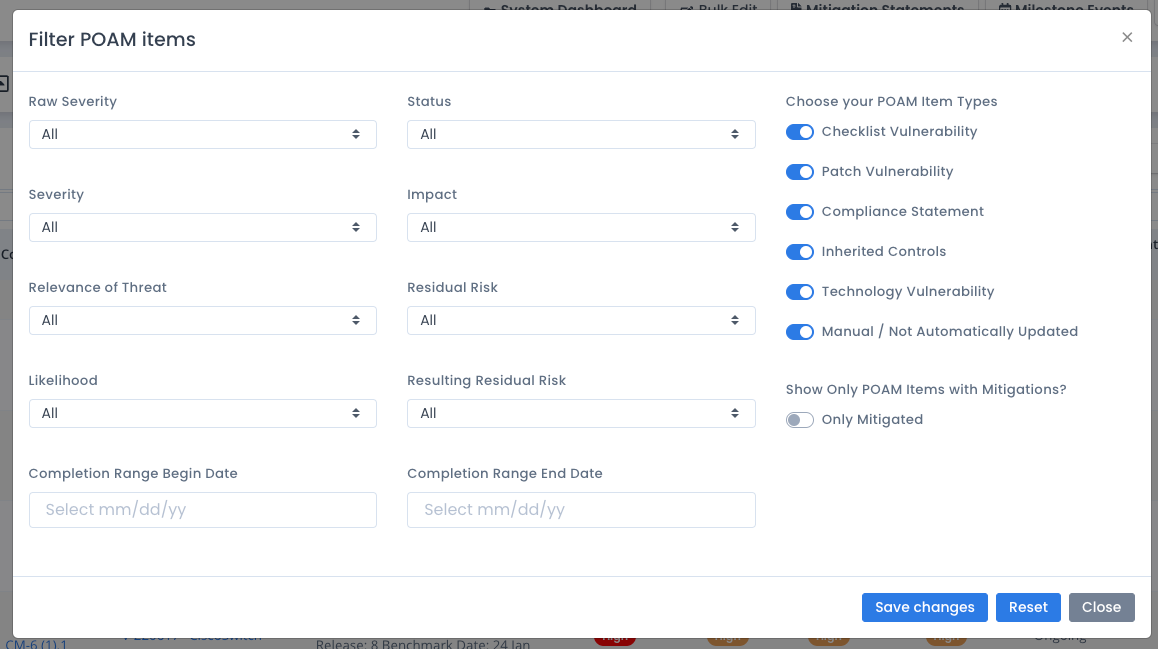
You can click the Filter button and open a filter to view specific POAM entries. Select the severity, status, impact, and other items and click the Save changes button to set the filter and refresh the page.
The “Choose your POAM Item Types” allows you to filter the POAM based on the item automatically linking to a checklist vulnerability, patch vulnerability, or other item listed. The “Manual / Not Automatically Updated” are for those items that are manually added, as well as those items linked to checklists or other items in the POAM listing that have had their linked item deleted. This can be a checklist deleted, a hardware device deleted, or other items removed from your system package.
Updating POAM Records Directly
If you have POAM Editor permissions, you can click the ... menu next to each POAM item and a popup editor appears. You can add information such as comments, severity, likelihood, comments, mitigations, linked milestone record, and the like. The dropdowns when saved with a value will color code the data in the table and the details view (click the green + icon).
Setting the Resulting Risk also will change the sort order as shown above. This will allow you to specify those items that are the riskiest at the top so you can see them, act on them, and work to minimize the issues in proper priority order.
There is also a slider for “Accept Risk” that you can choose if the POAM item is currently Ongoing. The item will be marked as accepted and the date of acceptance will be saved. You can slide this to the off position to return it back to Ongoing. The status and the date will be exported in the MS Excel file as well.
There is some automation built into the POAM entries. As you select Severity and Relevance of Threat, based on those values of Very High to Very Low the Likelihood is automatically set based on NIST rules on risk. This value can be set differently. But it will default when not filled in to a calculation based on Severity and Threat. This is only done when the Likelihood is not already set.
In the same way, as you select Likelihood and Impact, the Residual Risk is automatically set based on those values of Very High to Very Low from those fields. Just as stated above, this value can be set differently. But it will default when not filled in to a calculation based on Likelihood and Impact. This is only done when the Residual Risk is not already set.
Updating POAM Records Automatically
There are several automated ways the POAM items are updated. The data that is updated includes comments and status for existing items.
For new items from newer/updated checklists or new patch vulnerabilities from scans, all data is added the same way as if you just clicked the “create” button for the POAM. A patch vulnerability from a new server or a new item of an existing server will create a POAM record. And any open or “not reviewed” checklist vulnerability will also create a new POAM record.
Any patch vulnerability scan upload, checklist upload, checklist upgrade, technology vulnerability upload or import, or vulnerability editing through OpenRMF® Professional may also possibly affect POAM items for status, completion, and comments. This data is automatically updated from checklists and patches to the POAM to keep data in sync and consistent.
A new patch scan or technology vulnerability scan uploaded with vulnerabilities no longer present will render that corresponding POAM item Completed with the date. And any checklist vulnerability whose status changes to “not a finding” or “not applicable” also will be marked Completed with the date. If the checklist vulnerability is “not reviewed” or marked “open” it is added or updated to the POAM listing as well.
This in essence creates a live POAM that will include the most up-to-date information matching your checklists, compliance scans, and patch scans within your system package. A detailed reason why the POAM record was updated is included in the “reason for update” field to ensure you know why the update happened.
If you edit a comment on the POAM side, that comment is also added to the checklist vulnerability corresponding to the POAM entry as well automatically in the reverse direction as above. This keeps data in sync and consistent.
Regardless of the way you edit the POAM items, automatically or manually, there is bidirectional communication to keep all those files in sync automatically.
Rules for Risk, Residual Risk, and Your Organization
Most organizations have a way to classify the severity, allow mitigations, and mix the likelihood and impact with recommendations to get to the final overall residual risk. This will result in your risk classifications looking like the green, yellow, orange, and red risk chart highlighting Likelihood and Impact/Consequence. The POAM gives you the data. The rules on how you set and use the data is up to you and your organization.
NIST 800-37 Rev 2 https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final and https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-37r2.pdf have information spelled out on how to evaluate and assess the risk items you specify in your POAM. Use that information along with your organizational rules to make sure you specify your risk correctly.