Custom Template Information
Custom Templates created in OpenRMF® Professional allow you to use the same checklist construct familiar to RMF, FedRAMP, or GovRAMPTM for your particular needs. You can create a new checklist to match to the Program Management or Physical Security controls required for accreditation, but that are not done with automation or with DISA or CIS based checklists.
You also can create custom checklists to match to cloud computing architecture that are not host specific, such as an AWS S3 bucket, AWS EBS storage, Azure AKS Kubernetes infrastructure and the like. You also can create a custom checklist to ask questions on documentation and processes you must track for RMF, FedRAMP, or any cyber compliance framework you have loaded in your installation. You are only limited by your imagination.
Only an Administrator or Template Administrator can create a custom checklist. But once created, anyone using OpenRMF® Professional can use that template. The templates also can be saved and downloaded as checklist files just like other templates and checklists throughout the application that open using regular checklist viewing applications like STIG Viewer.
How Custom Templates are Created
If you are an Administrator or Template Administrator, from the Template listing page you can click the Create Custom Template button. The screen just below appears and lets you specify a title, description, version, release and other information. It also lets you specify if this is a template that will not specifically relate to a host. This could be a template that relates to processes, procedures, documentation, or even cloud computing resources that are general and not host specific.
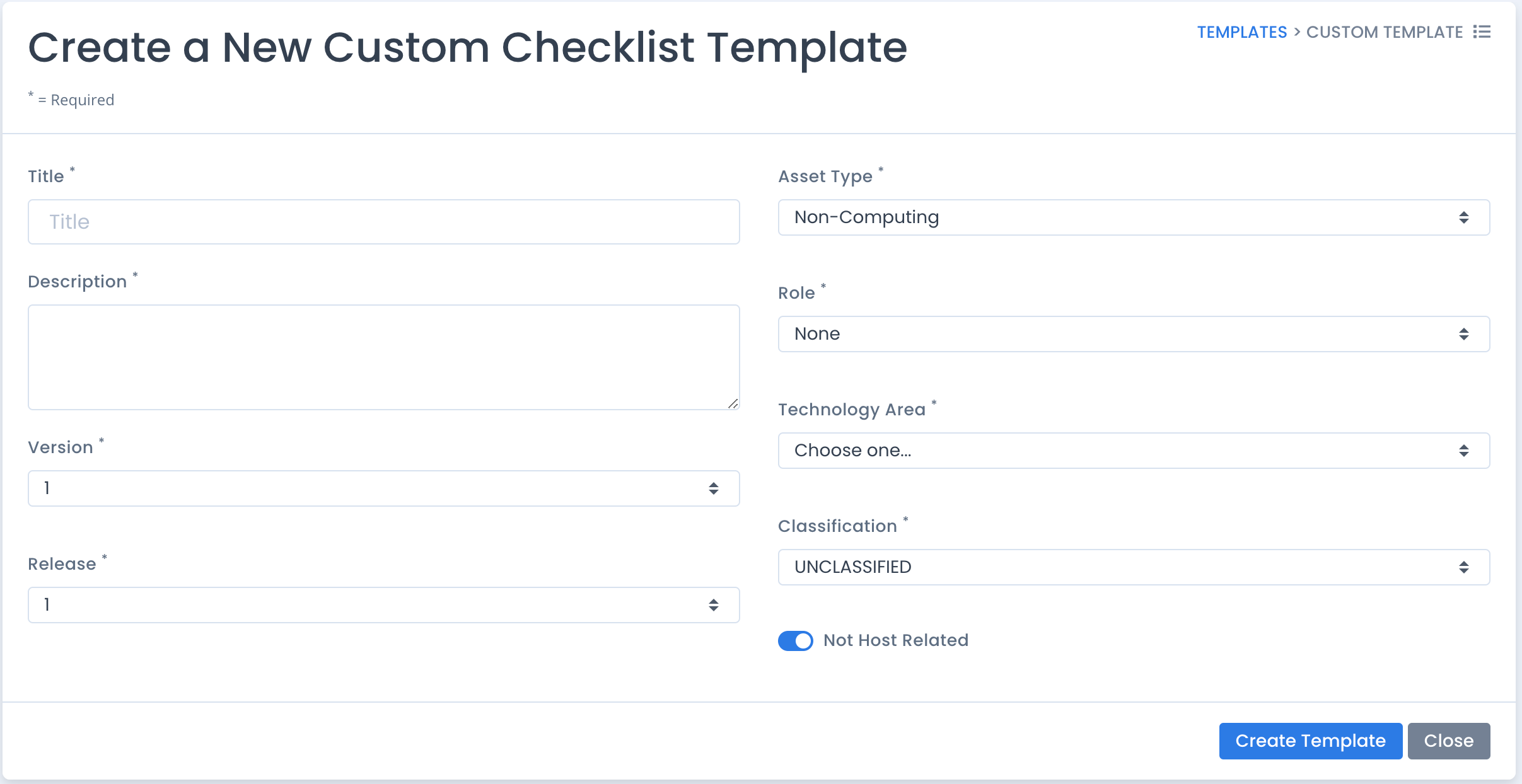
Fill out all fields and then click the Create button. This takes you to the familiar “Template Record” type of page but with some extra editing features. Scroll to the bottom to see the area you can add vulnerability information.
Setting the Vulnerability and STIG Prefixes
When uploading or manually creating vulnerability entries for your custom checklist, you can set the prefix for the vulnerability IDs, STIG IDs, and STIG Names for those entries. The actual number is generated internally and kept as a “one up” counter. However, the prefix you can determine for yourself. The default is “ORMF”.
To set that, from the custom template page for your template click the Update Details button. The Vulnerability Prefix, STIG ID Prefix and STIG Name Prefix fields show in the middle of the popup screen where you can edit the prefixes. Click the Save button at the bottom of that window. From there forward, your newer vulnerabilities will use those prefixes you set.
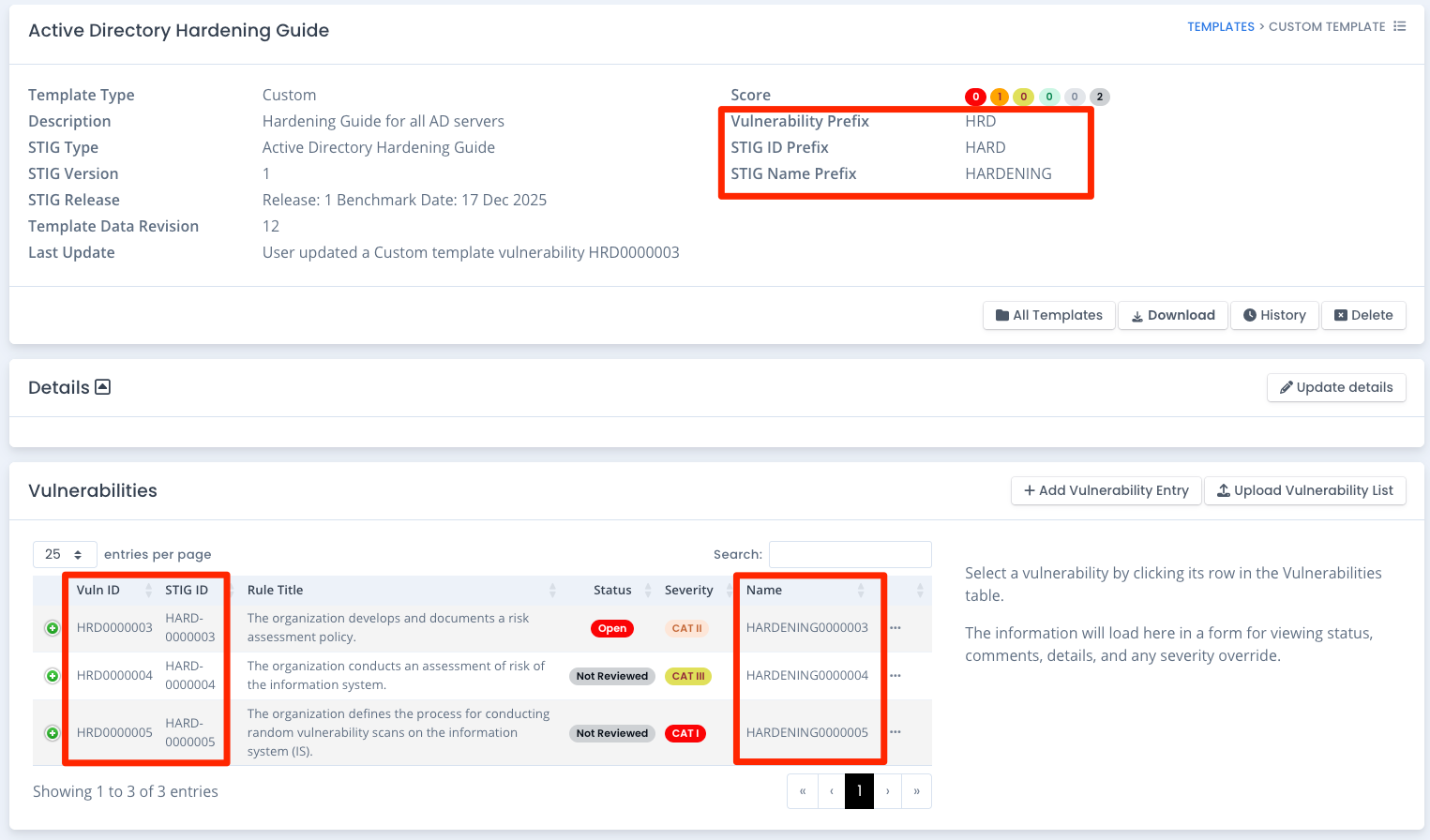
How to Upload Vulnerability and NIST Control Information from a File
You can quickly add multiple vulnerability entries in a custom checklist by using the approved format of the vulnerability listing. Download a Sample XLSX as a starting point for uploading a spreadsheet or CSV file. Or see below for the JSON format.
This allows you to quickly add rule title, severity (high, medium, low), check content, fix text, discussion, as well as 1 or more CCIs comma separated in a curated list for easy custom checklist creation.
The JSON format of the data allowed is shown below.
[
{
"Rule Title": "The organization develops and documents a risk assessment policy.",
"Severity": "medium",
"Check Content": "Check that the organization has developed a documented risk assessment policy and procedures to carry out that policy. Ensure that it addresses all issues required in the discussion and this information is readily available to all roles of personnel required in the organization. Also ensure this information is reviewed per the required frequency documented by the organization.\n\nIf any of this is not done, this is a finding.",
"Fix Text": "Create a risk assessment policy and procedures to carry out that policy and document all aspects of that. Ensure that it addresses all issues required in the discussion and this information is readily available to all roles of personnel required in the organization. Make sure it is reviewed and that required frequency is documented by the organization.",
"Discussion": "The organization develops and documents a risk assessment policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance.\n\nThe organization disseminates a risk assessment policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance to organization-defined defined personnel or roles.\n\nThe organization develops, documents and disseminates procedures to facilitate the implementation of the risk assessment policy and associated risk assessment controls to defined personnel or roles.\n\nThe organization reviews and updates the current risk assessment policy and procedures in accordance with a defined organization-defined frequency.",
"CCIs": "CCI-001037, CCI-001038, CCI-002368"
},
{
"Rule Title": "The organization conducts an assessment of risk of the information system.",
"Severity": "low",
"Check Content": "Check that the organization has done or is going to do a risk assessment and document the information accordingly. Ensure the results are put into a predefined plan or report and sent to all required personnel. And there are definitions on the frequency for updated risk assessments required based on time, changes, or other conditions laid out.\n\nIf any of this is not done, this is a finding.",
"Fix Text": "Conduct a risk assessment for the IS and document it in the correct plan or report. Then review it with all required personnel after they receive the report or plan and review it. Update the risk assessment when required and document the updated results again in the required document and disseminate appropriately.",
"Discussion": "The organization conducts an assessment of risk of the information system and the information it processes, stores, or transmits that includes the likelihood and magnitude of harm from the unauthorized access, use, disclosure, disruption, modification, or destruction.\nThe organization defines the organizational document in which risk assessment results are documented (e.g., security plan, risk assessment report) and documents risk assessment results in the organization-defined document.\n\nThe organization reviews risk assessment results on an organization-defined defined frequency and disseminates risk assessment results to organization-defined personnel or roles.\n\nThe organization updates the risk assessment on an organization-defined frequency or whenever there are significant changes to the information system or environment of operation (including the identification of new threats and vulnerabilities), or other conditions that may impact the security state of the system.",
"CCIs": "CCI-001053, CCI-001052, CCI-001051, CCI-001050"
},
{
"Rule Title": "The organization defines the process for conducting random vulnerability scans on the information system (IS).\t",
"Severity": "high",
"Check Content": "Check that the organization defines a process for conducting vulnerability scans on IS and hosted applications with a specific frequency. Ensure scans are conducted when new vulnerabilities possibly affecting the IS are identified and reported. And that they use correct and relevant vulnerability scanning tools across OS, process, procedure, software and configuration where appropriate and applicable and measure their impact.\n\nIf any of this is not done, this is a finding.",
"Fix Text": "Define the process for conducting vulnerability scans on IS and hosted applications with a specific frequency. Ensure scans are conducted when new vulnerabilities possibly affecting the IS are identified and reported. Use vulnerability scanning tools across OS, process, procedure, software and configuration where appropriate and applicable and measure their impact.",
"Discussion": "The organization defines the process for conducting random vulnerability scans on the information system and hosted applications.\n\nThe organization scans for vulnerabilities in the information system and hosted applications in accordance with the organization-defined process for random scans in an organization-defined frequency.\n\nThe organization scans for vulnerabilities in the information system and hosted applications when new vulnerabilities potentially affecting the system\/applications are identified and reported.\n\nThe organization employs vulnerability scanning tools and techniques that facilitate interoperability among tools and automate parts of the vulnerability management process by using standards for: enumerating platforms, software flaws, and improper configurations; formatting checklists and test procedures; and measuring vulnerability impact.\n\nThe organization analyzes vulnerability scan reports and results from security control assessments.\n\nThe organization remediates legitimate vulnerabilities in organization-defined response times in accordance with an organizational assessment risk and defines response times for remediating legitimate vulnerabilities.\n\nThe organization shares information obtained from the vulnerability scanning process and security control assessments with organization-defined personnel or roles to help eliminate similar vulnerabilities in other information systems (i.e., systemic weaknesses or deficiencies).",
"CCIs": "CCI-001641"
}
]
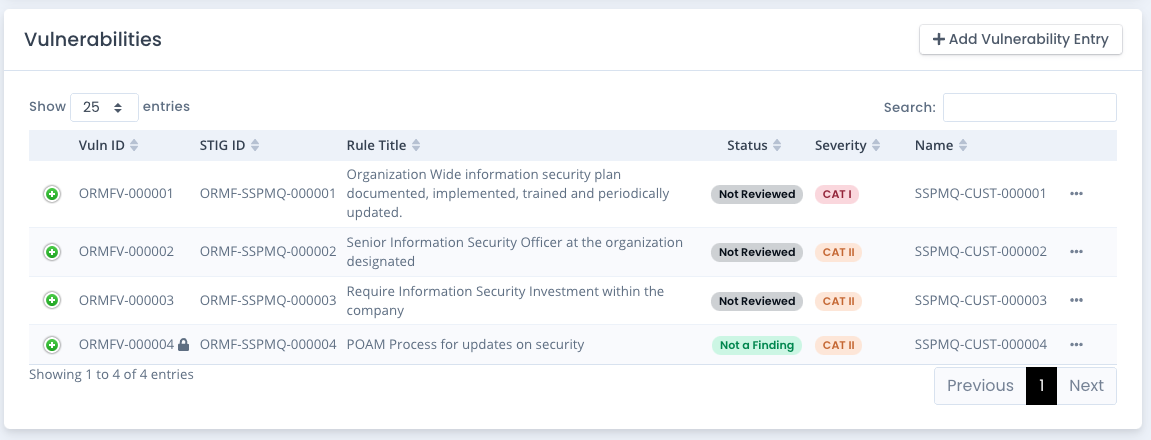
How to Manually Add Vulnerability and Control Information
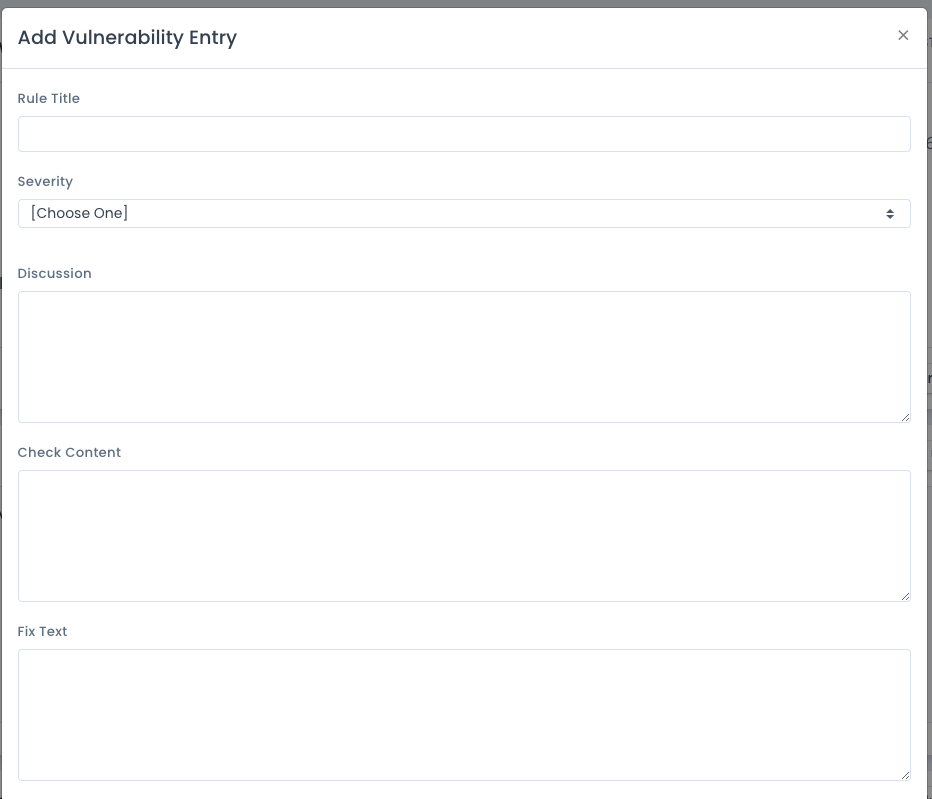
To add a custom vulnerability entry with rule title and check content, click the Add Vulnerability Entry button. A screen like the below image appears. Fill out the rule title, choose severity, and enter the discussion, check content and fix text as you would see for a normal vulnerability entry on any other checklist.
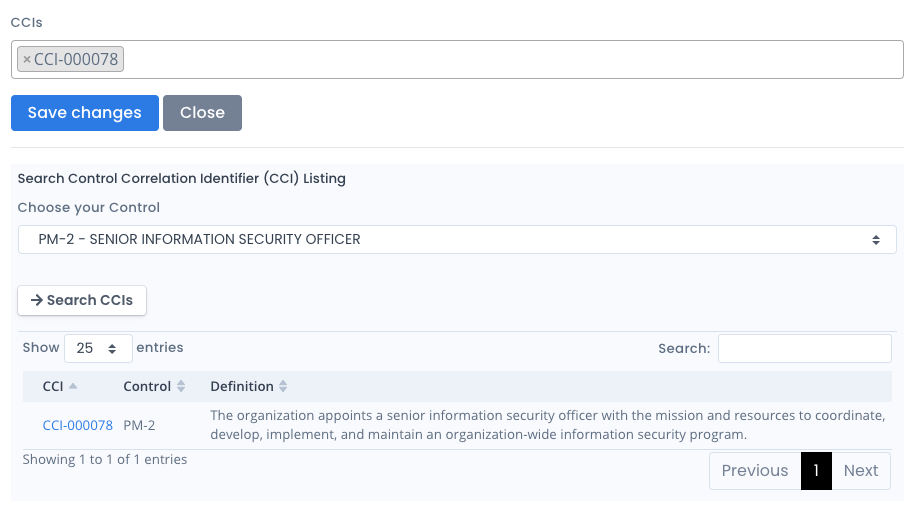
To link this vulnerability to a CCI which gives you the link to the corresponding required control, scroll to the bottom of the Vulnerability Entry window. Click the Cearch CCIs button and a listing appears for all CCIs (default or manually created) listed in your installation. Click the linked CCI to include it in the CCIs input box on this form. When done adding all relevant CCIs click the Save button. Note that this CCI will link to whatever control within your framework used for the system package where this custom checklist is added.
As you add and edit vulnerabilities you will see the vulnerability listing appear in the table. From here you can edit the field data, or you can edit the normal data as on other templates such as status, comments, and details. You also can choose to Lock that vulnerability after filling out the details and comments and the entry will be locked by default. Any checklist created from this template will also automatically have that vulnerability on the checklist filled out and locked.
Updating the Version and Release of Custom Templates
If you are making major changes to your custom template or adding/removing vulnerabilities you should update the release and/or version of the checklist. You can do this by clicking the “Update details” button on the main custom template page. Here it will let you select the next release or version of the checklist. As with other areas of OpenRMF® Professional, the older template information is saved and available through the History button.
What you can do with Custom Templates
If you select one or more templates in the listing you can bulk download them all into a ZIP file locally. All the .ckl or .cklb files that you selected will be in that ZIP file. You also can create new checklists from them or copy to other Organizational or System Package templates.
Copying them to other Templates
Your Custom Templates can also be copied into other templates for another Organizational or even System Package templates. System Package templates require you to have a “Create Template” group permission in that system or you will not see the option to copy to a system template. Once copied they are independent and can be updated and edited unto themselves. You may want to do this to customize templates as has been discussed in other areas of the help sections.
Making new Checklists from Custom Templates
If you have any “Create Checklist in a System Package” permissions you can select a Custom template from the listing and choose the “Create Checklist” from the bulk menu item just above the table listing to the right. If you click the Apply button you can choose the system and then a checklist of that type is created in that system.
You will need to update any information such as hostname, FQDN, role, etc. for the checklist inside the system listing.