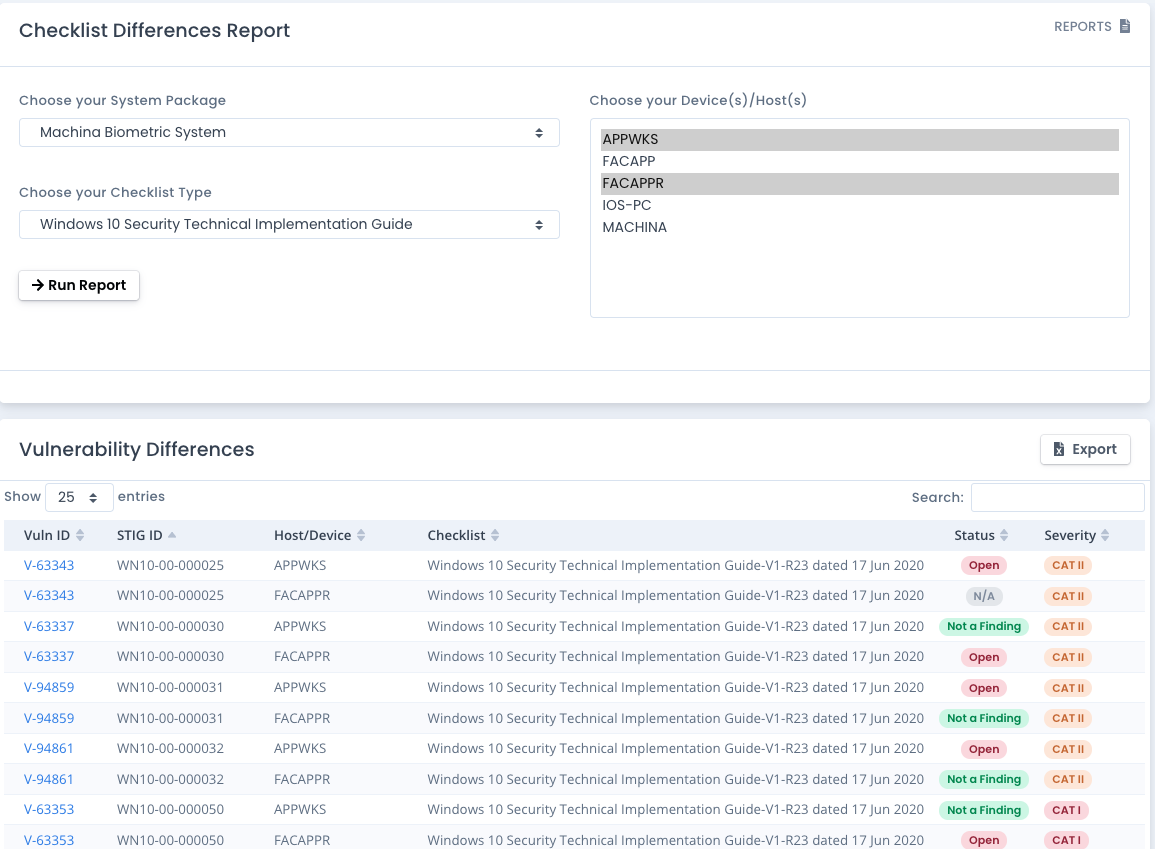
Run the Checklist Differences Report
This report shows items differences in vulnerabilities across Checklists based on type and device name. Choose the system package, the type of checklists and then at least 2 devices to compare. The results will compare the status of the vulnerability items to let you quickly note discrepancies and differences to investigate across those devices in your system package.
Where the Data Comes From
This data comes from all active checklists in your system package (i.e. you have not deleted them). Each checklist has a list of multiple vulnerabilities and their status as well as Category or Severity. That data is pulled from your checklists and put into the reporting database by vulnerability so reports like this can come back quickly and easily. As vulnerabilities are updated, they are versioned in the checklist database and the final data is parsed and updated in the vulnerability report database. The Technology Area of your checklist must be specified for this report to work well.
Why Run this Report
This report shows you quick differences in vulnerabilities by checklist type across devices.