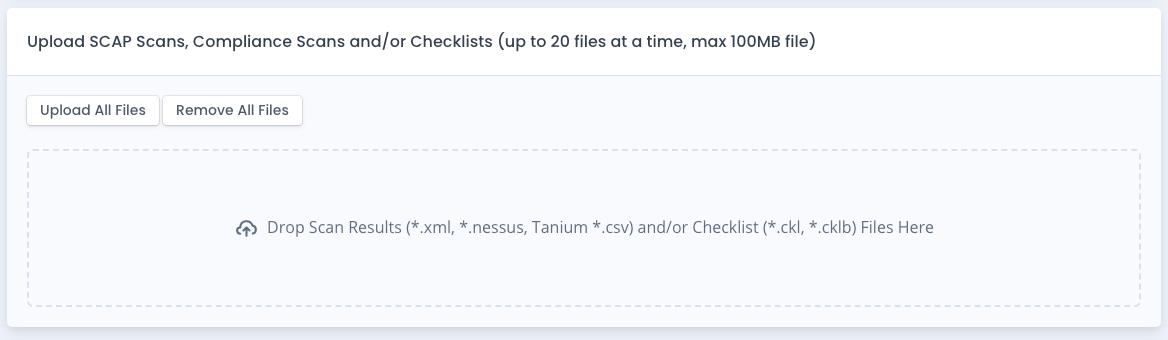
Loading Compliance Scans or Checklists
You can upload a new (i.e. add) or updated checklist or scan into OpenRMF® Professional to generate or update checklist records. To add checklists to a Team Subpackage you need the “Checklist Creator” group permission for that system. For editing you only need the “Checklist Editor” permission. You can go into the team subpackage and then click the “Upload” button just above the table listing all checklists.
On this screen you can add a .ckl or newer .clkb checklist file you have or one of the below listed formats for SCAP and Audit Compliance scans that automatically turn into checklists. You can upload up to 20 files (checklist and/or scan results) at one time. The maximum file size is 100 MB.
Note that Checklists in OpenRMF® Professional match a checklist type, a hostname (hostname is optional but recommended), as well as the web or database information on site and instance (if used). Those 5 items within a System Package determine the uniqueness on checklists, SCAP, Audit Compliance uploads and if your upload creates a new checklist entry or updates an existing one.
CKL or CLKB files that have combined checklist types or STIG types in a single file can still be uploaded. They are then separated into separate checklist records, one for each STIG or checklist type along with the other unique items mentioned above.
SCAP *.xml results already contain only one matching host and checklist type. Tanium SCAP *.csv as well as Nessus/ACAS Audit Compliance scans (*.nessus) can contain multiple hosts and checklist types in their results you upload. Checklists generated will be one-to-one in the System Package Checklist Listing from the results upload.
Available formats we ingest:
- Checklist (CKL) file from STIG Viewer v2 or v3, or EvaluateSTIG
- Checklist (CKLB) file from STIG Viewer v3 or EvaluateSTIG
- DISA SCAP XCCDF using a DISA Benchmark
- Tenable Nessus SCAP
- OpenSCAP v1.2 or v1.3 using a DISA Benchmark
- Rapid7 Nexpose SCAP using a DISA Benchmark
- HBSS SCAP using a DISA Benchmark
- Tanium SCAP CSV results using a DISA Benchmark
- Tenable Nessus Audit Compliance with DISA Benchmark
- Tenable Nessus Audit Compliance with CIS Benchmark
- Rapid7 Nexpose scan with CIS Benchmark (1 profile per result currently)
- RapidFort JSON from Container Image scan with DISA Benchmark
Note: If you upload a scan or checklist file of a new host/checklist type combination and are a Checklist Creator in the team subpackage, the checklist will be added to the team subpackage and processed only if it is not already somewhere else within the larger system package.
Once the checklist is uploaded and processed, there are a few things that happen behind the scenes.
- A record is made matching this checklist to the system package
- The checklist score is calculated and saved for this checklist
- The system package checklist score across all checklists is updated and saved with this system
- The reporting system parses the checklist and saves off each vulnerability into a reporting structure for later use with reports and searching
If this is a “update” of an existing checklist in this system, it also does a few more things
- It creates a checklist history record
- It creates a checklist score history record
- It creates a system package score history record
Upload Scan Results
When you upload a scan result the application matches the benchmark used for the scan up to the matching template in the system. More information on this detailed process is in the SCAP Scan Help Area and Audit Compliance Scan Help Area for checklists. Once the checklist is made from the scan the rest of the process listed above happens and the application returns to allow more uploads. Or you can go back to the system package page.
Upload a Checklist (CKL or CKLB) file
When you upload a regular checklist .ckl or .cklb file, the system parses and makes sure the checklist is valid. Then it saves the data and follows the process outlined above. The application returns to allow more uploads or you can go back to the main system package dashboard.
How POAM Items are Added and Updated
If you have any compliance items that are Open or Not Reviewed, your POAM will add them when you generate a new POAM. It grabs all the relevant data and fills in the POAM entry for that checklist vulnerability. It also links the checklist vulnerability data that caused that entry to be created. So when viewing the POAM, you can click “View Checklist Vulnerability” and it will open the checklist data and filter on that particular entry. That gives you bi-directional traceability for the POAM and the Checklist Vulnerability data.
If you have the POAM already generated, any new item from a compliance scan marked Open or Not Reviewed not already in the system package patch data is added to the POAM with the correct severity. Any item previously in the system package vulnerability data as Open or Not Reviewed but NOT in the most recent (could have been dropped) based on the hostname and checklist type will be marked as Completed. It will still be maintained in the system package POAM data. Any new Open or Not Reviewed item from that hostname and checklist type is added. Any item previously Open or Not Reviewed marked as Not a Finding or Not Applicable will be marked as Completed on the POAM.
When you choose to export the POAM to MS Excel and select the 90, 180, or 360 day option the POAM item closed will appear if updated within that time period.